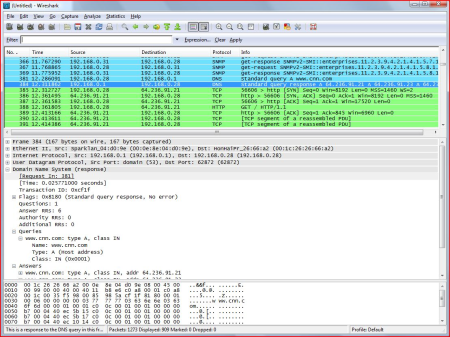
Common Windows Error Codes and How to Fix them!
Below is a list of the most common error codes that you may face while
using Windows and its basic components. Some solutions have been
provided for you to try to solve them. You should also note that some
require the assistance of a computer technician and you should
not try to fix them yourself as they could seriously damage your computer system.
Error Message: Connection Successful!
Solution: Does not require any action.
Error Message: System cannot find specified file
Solution: You should reinstall NCP & DUN
Error Message: Access Denied
Solution: 1. Ensure that you have entered the right username and password in the field labeled "domain" for NT/2k
2. Check that the option "accept any authentication including clear text" is activated
Error Message: Invalid Procedure Call
Solution: Dialup and Network components must be installed again
Error Message: Stack Overflow
Solution: 1. Try cold booting your computer
2. If this does not work, the problem might come from your RAM or the Swap file
Error Message: The system cannot find the specified device
Solution: 1. Ensure that the right modem has been selected
2. If it does not respond, try to reinstall it
3. You can also try to reinstall NCP/DUN/RAS
Error Message: No more connections are allowed
Solution: 1. Someone else might have connected under your account
2. If you have been ghosted on the server, your Internet Service Provider can bump the ghost program off
Error Message: Invalid Proper Value
Solution: 1. Autodial should be pointed to the correct dialler
2. Else, set up the dialler again
Error Message: An operation is pending
Solution: 1. You should first try rebooting your computer
2. Ensure that no other program is using your modem
3. Else, press Ctrl-Alt-Delete and if RNAAPP loads, contact a technician to fix this problem
4. Make sure that your computer is Spyware free
Error Message: The port handle is invalid
Solution: 1.
Select the modem's COM port and under the Diagnosis section, open "More
Info". You should reboot your computer if you are able to get ATI
responses, remove the erroneous init string or enter ATZ as the init
2. You can also reinstall your modem
3. Else press Ctrl-Alt-Delete and if RNAAPP loads, contact a technician to fix this problem
4. Your Dialup Networking should be reinstalled together with its components
5. Your modem might not be working properly. You should then consult your computer manufacturer
Error Message: The port is already open
Solution: 1. Try to reboot your computer
2. Ensure that no other program is using the modem
3. Else press Ctrl-Alt-Delete and if RNAAPP loads, contact a technician to fix this problem
4. Try uninstalling the AOL Adapters in the Network Control panel and reboot your computer. Install your Dialup Adapter again
5. Remove the erroneous init string or enter ATZ as the init
6. If you have Quicken 2000, deactivate the Quicken Download Manager
7. Try installing your modem again
8. Make sure that your computer is Spyware free
Error Message: Caller's buffer is too small
Solution: 1. Ensure that your port is not configured to a low speed
2. In your "Port Settings", ensure that FIFO is not set to low
3. Try reinstalling your Dialup Networking together with its components
4. If you are still having problems, contact your computer manufacturer
Error Message: Wrong information specified.
Solution: 1. Ensure that the are no outages in your area
2. Try to enter the username and password again
3. Set up the dialler again
4. Your Dialup Networking should be installed again together with its components
5. You can also try to reinstall your modem
Error Message: Cannot set port information.
Solution: 1. Ensure that the are no outages in your area
2. Try to enter the username and password again
3. Set up the dialler again
4. Your Dialup Networking should be installed again together with its components
5. You can also try to reinstall your modem
Error Message: The port is not connected.
Solution: 1.
Select the modem's COM port and under the Diagnosis section, open "More
Info". You should reboot your computer if you are able to get ATI
responses, remove the erroneous init string or enter ATZ as the init
2. You can also reinstall your modem
3. Else, press Ctrl-Alt-Delete and if RNAAPP loads, contact a technician to fix this problem
4. Your modem might not be working properly. You should then consult your computer manufacturer if the problem persists.
Error Message: The event is invalid.
Solution: 1. If this problem arises while dialling up to the internet, verify that the settings of the event log have been correctly set
2. Try rebooting your system and ensure that the dialler/network settings have been correctly configured
3. Else, install RAS/DUN again
Error Message: The device does not exist.
Solution: 1. Check that the right modem is set in the dialler
2.
Ensure that you are using the right modem drivers by checking the modem
diagnostics. If it's not the case, set up the correct drivers.
3. Reinstall the dialler
4. Your modem might not be working properly. Try reinstalling it
5. You should consult your computer manufacturer if the problem persists
Error Message: The device type does not exist.
Solution: 1. Check that the right modem is selected in the dialler
2.
Ensure that you are using the right modem drivers by checking the modem
diagnostics. If it's not the case, set up the correct drivers
3. Your modem might not be working properly. Try reinstalling it
4. You should consult your computer manufacturer if the problem persists
Error Message: The buffer is invalid.
Solution: 1. Ensure that your port speed is set to low in the modem properties
2. In your "Port Settings", check that FIFO is not set to low
3. Reinstall the dialer again
4. Else, reinstall RAS/DUN
5. You should consult your computer manufacturer if the problem persists
Error Message: The route is not available.
Solution: 1. Try to reboot your computer
2. Ensure that you set the right configurations for the dialer and network settings
3. Else, install the network components again
4. If you are using a LAN connection, consult your system administrator
Error Message: The route is not allocated.
Solution: 1. Reboot your computer
2. Ensure that you set the right configurations for the dialler and network settings
Error Message: Invalid compression specified.
Solution: 1. Try to reboot your computer
2. Else, add &K3 to the extra settings.
3. If this still does not solve the problem, add &K3
4. You can also try to reinstall the modem
Error Message: Out of buffers.
Solution: 1. Ensure that our port speed is not too low
2. Try to install your modem again
Error Message: The port was not found.
Solution: Try to install your modem drivers
Error Message: An asynchronous request is pending.
Solution: 1. Reboot your computer
2. Try to install your modem drivers again
Error Message: The port or device is already disconnecting
Solution: 1. Wait until your modem disconnects properly
2. If this operation is taking too long, reboot your computer
Error Message: The port is not open.
Solution: 1. Reboot your computer
2. Ensure that no other program is making use of the modem
Error Message: The port is disconnected.
Solution: 1. Reboot your computer
2. Ensure that no other program is making use of the modem
Error Message: Cannot open the phone book file.
Solution: Install Blue Frog connection software again
Error Message: Cannot load the phone book file.
Solution: Install Blue Frog connection software again
Error Message: Cannot find the book entry.
Solution: Install Blue Frog connection software again
Error Message: Cannot load a string
Solution: 1. Try to reboot your system
2. Install Blue Frog connection software again
Error Message: Cannot find key
Solution: Install Blue Frog connection software again
Error Message: The port was disconnected
Solution: 1. Install Blue Frog connection software again
2. Try to install your modem drivers again
Error Message: The port was disconnected by the remote machine.
Solution: 1. Install Blue Frog connection software again
2. Try to enter an alternate Access Number
3. Try to install your modem drivers again
Error Message: The port was disconnected due to hardware failure.
Solution: 1. Install Blue Frog connection software again
2. Try to reinstall your modem drivers
3. Try to use an alternate modem
4. Else, replace your current modem with a new one
Error Message: The port was disconnected by the user.
Solution: 1. Ensure that the right Access Number is being dialled
2. Try to reboot your computer
Error Message: The structure size is incorrect.
Solution: 1. Try to reboot your computer
2. Install Blue Frog connection software again
Error Message: The port is already in use or is not configured for Remote Access dialout.
Solution: 1. Try to reboot your computer
2. Else, try to reinstall your modem drivers
Error Message: Cannot register your computer on the remote network.
Solution: 1. Try to check your network settings and modify your computer name
2. Install the network control panel again
Error Message: Unknown Error
Solution: 1. Try to reboot your computer
2. Install Blue Frog connection software again
3. Else try to reinstall your modem drivers
Error Message: The wrong device is attached to the port
Solution: Check in your settings if you have chosen the right modem
Error Message: The string could not be converted
Solution: 1. Try to reboot your computer
2. Install Blue Frog connection software again
Error Message: The request has timed out.
Solution: 1. Try to reboot your computer
2. Install Blue Frog connection software again
Error Message: Internal authentication error.
Solution: 1. Try to reboot your computer
2. Install Blue Frog connection software again
3. Else, try to reinstall your modem drivers
Error Message: The Remote Access server is not responding.
Solution: 1. Check that your connection and network settings have correctly been configured
2. Ensure that the modem has been correctly set up and look for updated drivers
3. Set FIFO buffers to a lower speed and ensure that you have unchecked the option "Only connect at this speed"
Error Message: The line is busy
Solution: Ensure that your Access Number is still active and is correctly dialled
Error Message: There is no answer.
Solution: 1. First of all check that your phone lines are correctly plugged in
2. Ensure that the Access Number is correct
3. Else, try another Access number
4.
If you are trying to make use of your connection in a bad weather, this
might be the source of the problem. Wait until it calms down and try
again
5. Else, install your modem drivers again
6. If the problem persists, you might need to contact your ISP
Error Message: There is no dial tone.
Solution: 1. First of all check that your phone lines are correctly plugged in
2. The cables might be damaged. Replace them and try again
3. Else, install your modem drivers again
4. If the problem persists, you might need to contact your ISP or a technician
Error Message: Access denied because username and/or password is invalid on the domain.
Solution: 1. Ensure that you have entered the right username and password
2. Make sure that your account is active and turned on
3. You might also try to enter another Access Number
4. If the problem persists, you might need to contact your ISP
Error Message: Hardware failure in port or attached device.
Solution: 1. Browse for and remove any Blue Frog init strings
2. Install Blue Frog connection software again
3. Else, install your modem drivers again
Error Message: PPP Timeout
Solution: 1. Try to reboot your computer
2. Ensure that you have entered the right username and password
3. You might try another Access Number
4. Install Blue Frog connection software again
5. Else, install your modem drivers again
Error Message: Remote PPP peer is not responding.
Solution: For Windows 2000/XP/Vista operating systems, ensure that the security setting for the dialler reads "Allow unsecured Password"
Error Message: The PPP link control protocol terminated.
Solution: For Windows 2000/XP/Vista operating systems, ensure that the security setting for the dialer reads "Allow unsecured Password"
Error Message: The connection attempt failed because the modem on the remote computer is out of order.
Solution: 1. Install Blue Frog connection software again
2. Install your modem drivers again
3. Else, install a new modem
Error Message: It was not possible to verify the identity of the server.
Solution: 1. Ensure that you are dialling the correct phone number
2. Verify the connection and Network settings
3. Ensure that you do not have an outage on the phone line
4. Ensure that you have correctly installed your modem and check for updated drivers
5. Set FIFO buffers to a lower speed and ensure that you have unchecked the option "Only connect at this speed"
Error Message: To dial out using this connection, you must use a smart card.
Solution: 1. Ensure that all authorisation is allowed in your connection settings in the Security section
2. Verify that you have correctly set the other dialler settings
3. Else, create the dialler again
4. You might need to use the Smart Card Reader as initially setup by the Network Administrator
Error Message: An attempted function is not valid for this connection.
Solution: Ensure that the dialler, not the one set up for LAN use though, has been properly installed and has the right settings
Error Message: The encryption attempt failed because no valid certificate was found.
Solution: You have to get a valid certificate by registering to the website http://windows.microsoft.com/...
Note: The
solution for the following problems is already provided in the error
messages. If you are still facing problems with them, either contact
your ISP or a technician to fix the problem.
Error Message: Network
Address Translation (NAT) is currently installed as a routing protocol,
and must be removed before enabling Internet Connection Sharing
Error Message: Internet
Connection Sharing cannot be enabled. The LAN connection selected as
the private network is either not present, or is disconnected from the
network. Please ensure that the LAN adapter is connected before enabling
Internet Connection Sharing.
Error Message: You
cannot dial using this connection at logon time, because it is
configured to use a user name different than the one on the smart card.
If you want to use it at logon time, you must configure it to use the
user name on the smart card.
Error Message: You
cannot dial using this connection at logon time, because it is not
configured to use a smart card. If you want to use it at logon time, you
must edit the properties of this connection so that it uses a smart
card.
Error Message: The L2TP connection attempt failed because there is no valid machine certificate on your computer for security authentication.
Error Message: The L2TP connection attempt failed because the security layer could not authenticate the remote computer.
Error Message: The
L2TP connection attempt failed because the security layer could not
negotiate compatible parameters with the remote computer.
Error Message: The
L2TP connection attempt failed because the security layer encountered a
processing error during initial negotiations with the remote computer.
Error Message: The L2TP connection attempt failed because certificate validation on the remote computer failed.
Error Message: The L2TP connection attempt failed because security policy for the connection was not found.
Error Message: The L2TP connection attempt failed because security negotiation timed out.
Error Message: The L2TP connection attempt failed because an error occurred while negotiating security.
Error Message: The Framed Protocol RADIUS attribute for this user is not PPP.
Error Message: The Tunnel Type RADIUS attribute for this user is not correct.
Error Message: The Service Type RADIUS attribute for this user is neither Framed nor Callback Framed.
Error Message: A connection to the remote computer could not be established because the modem was not found or was busy.
Error Message: A certificate could not be found that can be used with this Extensible Authentication Protocol.
Error Message: Internet
Connection Sharing (ICS) cannot be enabled due to an IP address
conflict on the network. ICS requires the host be configured to use
192.168.0.1. Please ensure that no other client on the network is
configured to use 192.168.0.1
Error Message: Unable
to establish the VPN connection. The VPN server may be un-reachable, or
security parameters may not be configured properly for this
connection.
Solution: 1. Check your ADSL line as it is probably not synchronized
2. Verify that your Security Options are correctly set in your connection options
3. Either your Network Card or your modem might not work properly. Contact a technician if the problem persists
Error Message: Operation aborted.
Error Message: Maximum length exceeded.
Error Message: Account expired.
Error Message: Network connection does not exist.
 Using
keyboard shortcuts can greatly increase your productivity, reduce
repetitive strain, and help keep you focused. For example, highlighting
text with the keyboard and pressing Ctrl + C is much faster than taking
your hand from the keyboard, highlighting the text using the mouse,
clicking copy from the file menu, and then putting your hand back in
place on the keyboard. Below are our top 10 keyboard shortcuts we
recommend everyone memorize and use.
Using
keyboard shortcuts can greatly increase your productivity, reduce
repetitive strain, and help keep you focused. For example, highlighting
text with the keyboard and pressing Ctrl + C is much faster than taking
your hand from the keyboard, highlighting the text using the mouse,
clicking copy from the file menu, and then putting your hand back in
place on the keyboard. Below are our top 10 keyboard shortcuts we
recommend everyone memorize and use. Make the most of your Windows Start screen tiles by adjusting the sizes, where they are located, and what is listed.
Make the most of your Windows Start screen tiles by adjusting the sizes, where they are located, and what is listed.




 Bill
Schlough, Senior Vice President and Chief Information Officer for the
San Francisco Giants, sensed mobile data demand was on a sharp rise as
early as 2009, which led his charge to create an extremely tech-friendly
atmosphere at AT&T Park, home of the San Francisco Giants. Leading
up to the 2010 baseball season, Schlough and his team already had an
AT&T Wi-Fi system in place, but worked with AT&T to install a
DAS to combat the data crunch coming from the nimble hands of
smartphone-wielding fans at the ballpark.
Bill
Schlough, Senior Vice President and Chief Information Officer for the
San Francisco Giants, sensed mobile data demand was on a sharp rise as
early as 2009, which led his charge to create an extremely tech-friendly
atmosphere at AT&T Park, home of the San Francisco Giants. Leading
up to the 2010 baseball season, Schlough and his team already had an
AT&T Wi-Fi system in place, but worked with AT&T to install a
DAS to combat the data crunch coming from the nimble hands of
smartphone-wielding fans at the ballpark.